
Zero Trust Target Level Requires Procurement & Implementation of UEBA Tooling
November 4, 2025
Federal Resources Corporation Announces Rebrand to FRC, Reflecting Expansion Beyond Federal Markets
November 18, 2025Macro vs. Micro Segmentation in a Zero Trust Architecture: Drawing the Fences
In today’s digital landscape, a breach is often a question of when, not if. The most devastating attacks don’t come from a single perimeter failure, but from lateral movement—when an attacker pivots from one compromised system to another, moving freely “East-West” inside the network. This reality demands the implementation of a Zero Trust Architecture (ZTA), where the architecture is designed assuming that a breach has already occurred.
One critical step in implementing ZTA is the practice of segmentation, or drawing granular “fences” around our digital assets. This is where understanding macro segmentation versus micro segmentation begins. Macro segmentation gives us the broad, foundational barriers, while micro segmentation provides the fine-grained, workload-specific control necessary to eliminate implicit trust. Knowing how to implement these two strategies is mandated in modern security frameworks like the DoD’s Zero Trust Target Level Activities.
The following DoD’s Zero Trust Target Level Activities mandate implementing a macro and micro-segmentation. In-depth discussion on all of these activities are available in our Zero Trust Target Level Network & Environment Activities downloadable white paper.
- Activity 5.3.1 – Datacenter Macro Segmentation
- Activity 5.3.2 – BCPS Macro Segmentation
- Activity 5.4.1 – Implement Microsegmentation
- Activity 5.4.2 – Application and Device Microsegmentation
To fully grasp the differences between these two segmentation strategies, it’s helpful to first understand the foundational layers of network communication, often referenced using the OSI (Open Systems Interconnection) model. While the OSI model has seven layers, for the purpose of network segmentation, we primarily focus on a few key ones:
- Layer 2 (Data Link Layer): Deals with physical addressing (MAC addresses) and local network communication within a broadcast domain. Think of switches operating at this layer. VLANs, which are a common form of macro segmentation, operate by logically separating traffic at Layer 2.
- Layer 3 (Network Layer): Handles logical addressing (IP addresses) and routing of data packets across different networks. Routers operate at this layer. Firewalls often enforce policies based on IP addresses at Layer 3.
- Layer 4 (Transport Layer): Manages end-to-end communication between applications, including port numbers (e.g., port 80 for HTTP, port 443 for HTTPS). Firewalls also enforce policies based on port numbers at Layer 4.
- Layer 7 (Application Layer): This is where user applications and network services interact. It deals with protocols like HTTP, DNS, SMTP, etc. Modern security controls, particularly those supporting micro segmentation, can analyze and enforce policies based on application-level context and content.

Understanding these layers is crucial because the “fences” we build with macro and micro segmentation operate at different points within this stack, enabling varying degrees of granularity and control.
The Core Differentiator: Granularity of Control
The primary factor creating the differentiation between macro and micro segmentation is granularity. It dictates the size and scope of the “fences” we erect around our digital assets, directly impacting the precision of our access control policies.
Macro Segmentation: The Large Fences (Predominantly Layer 2, 3, and 4)
Macro segmentation, often synonymous with traditional network segmentation or perimeter segmentation, involves dividing a network into broad, high-level zones based on organizational structure, department, or function. Think of it as creating large, distinct “neighborhoods” within your city, each with its own designated entry and exit points.
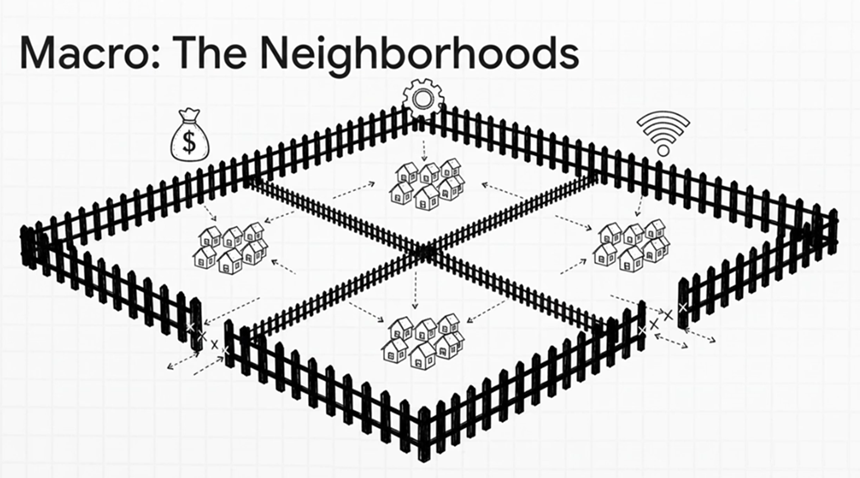
- What it is: This typically relies on traditional network security controls like VLANs (Virtual Local Area Networks) at Layer 2, subnets, physical or virtual firewalls, and Access Control Lists (ACLs) operating at Layer 3 (IP addresses) and Layer 4 (ports). Traffic is permitted or denied between these large, defined segments.
- Where we have larger “fences”: The “fences” here are substantial, encompassing entire departments (e.g., Finance, HR, R&D), major application environments (e.g., production, development, testing), or entire data centers. For example, a firewall might enforce a policy stating that traffic from the “Guest Wi-Fi” segment (defined by a Layer 2 VLAN and Layer 3 subnet) cannot access the “Production Server” segment. While this provides a strong outer barrier, a breach within one macro segment might not immediately compromise another, but lateral movement within that large segment remains a significant risk due to broader permissions. This internal, or ‘East-West,’ traffic is largely unconstrained, meaning an attacker who gains access to one workload can often move freely to other workloads within the same segment.
- Benefits: Easier to design and implement initially for broad strokes of security. Provides a good baseline level of security and can help meet compliance requirements for high-level data separation.
- Limitations: Offers limited protection against threats that have already breached the perimeter or are operating internally. Lateral movement within a segment is largely unconstrained, meaning an attacker who gains access to one workload within a macro segment can often move freely to other workloads within that same segment.
Micro Segmentation: The Smaller Fences (Predominantly Layer 3, 4, and 7, often Workload-Centric)
Micro segmentation, in contrast, focuses on isolating individual workloads, applications, or even specific processes within a network. It’s about creating highly granular, often software-defined, security policies that dictate communication down to the individual asset level. This is akin to building individual “houses” with their own perimeter fences within each neighborhood, or even individual “rooms” within each house, each with its own specific access rules.
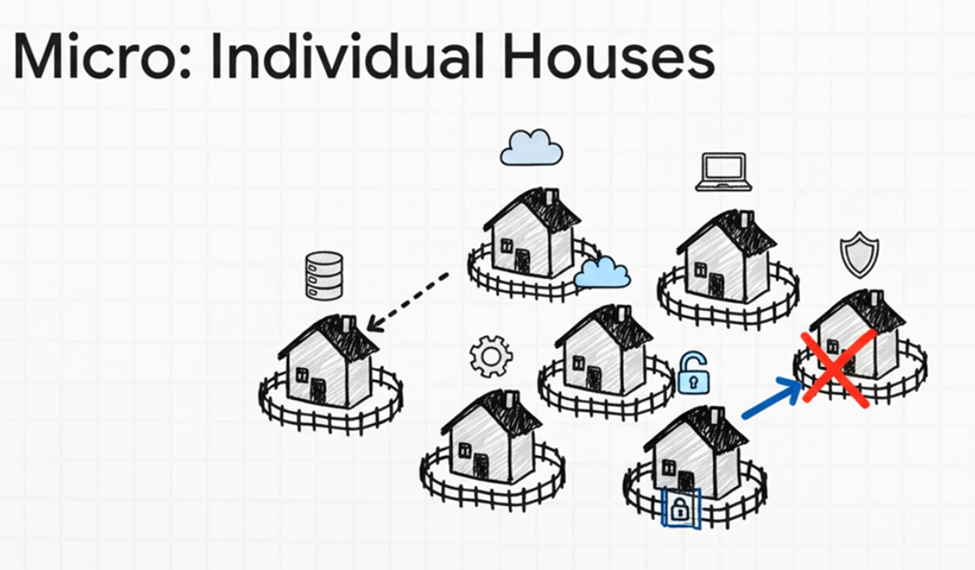
- What it is: Often implemented using host-based firewalls, hypervisor-level controls, or specialized software-defined networking (SDN) solutions. The power of a software-defined approach is that it decouples the security policy from the network topology. Policies are applied directly to workloads, defining what they can communicate with, and often leveraging identity and context (e.g., user identity, workload identity (via certificates or tokens), device posture, application state) rather than just static IP addresses and ports. This allows for highly precise policies that can operate at Layer 3 (IP), Layer 4 (port), and critically, Layer 7 (application protocol and context).
- Where we have smaller “fences”: The “fences” are significantly smaller and more numerous. They surround individual virtual machines (VMs), containers, specific application tiers (e.g., web server, application server, database server), or even individual processes. Communication is restricted to only what is explicitly necessary for the workload or application component to function. For instance, a policy might dictate that only the “Web Server A” workload can initiate a connection to “Application Server B” on a specific port, and only if User X is authenticated and their device is compliant, and the communication is specifically for the “Order Processing” application (Layer 7 context).
- Benefits: Dramatically reduces the attack surface by enforcing least privilege at the workload level. Contains breaches to the smallest possible blast radius, preventing lateral movement. Improves regulatory compliance by isolating sensitive data. Provides greater visibility into network traffic at a granular level.
- Limitations: More complex to design, implement, and manage due to the sheer number of policies. Requires a deep understanding of application dependencies and communication flows to avoid unintended service disruptions.
The Zero Trust Imperative
In a Zero Trust model, both macro and micro segmentation play vital roles. Macro segmentation provides the foundational, broad-stroke security by segmenting the network into large zones, often at Layer 2, 3, and 4. However, it’s micro segmentation that truly embodies the “never trust, always verify” principle, refining these defenses by isolating individual workloads and enforcing granular policies that extend to Layer 7 context. This ensures that even within a broadly “trusted” macro segment, no entity is implicitly trusted, and every communication is evaluated against a strict, contextual policy before access is granted.
Analogy:
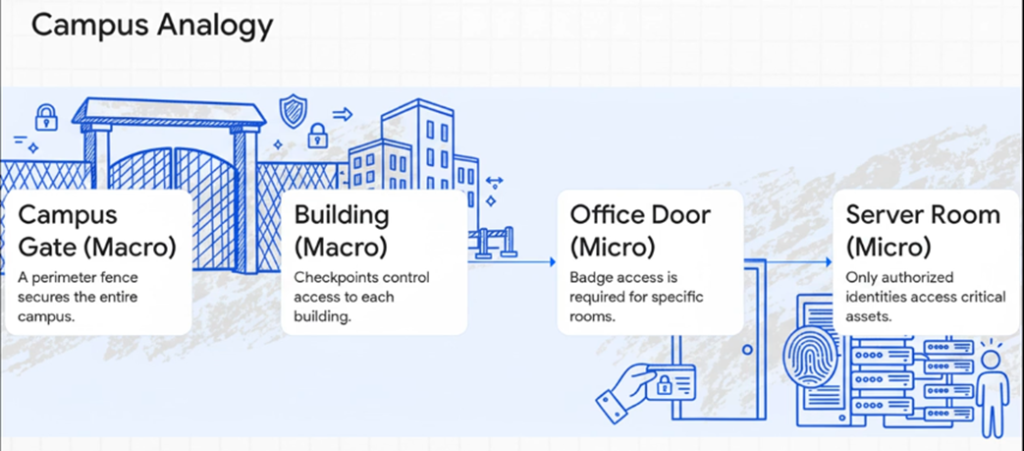
Consider a multi-building corporate campus.
- Macro Segmentation is like putting a strong perimeter fence around the entire campus, with security checkpoints at the main entrances to each building (e.g., the “R&D Building,” the “Finance Building”). These controls primarily operate at the building entrance level (similar to Layer 3/4 firewalls controlling traffic between subnets). If an unauthorized person gets past the main campus gate, they might still be contained within the campus, but once inside a building, they could potentially wander freely within that building.
- Micro Segmentation takes this further. Within each building, every office, every lab, and even every cubicle has its own access control system. Employees only have badge access to the specific rooms and areas they absolutely need for their job. This level of control goes beyond just building entrances; it looks at who is trying to access what specific room and why (similar to Layer 7 policies evaluating application context and user identity). If an attacker breaches the “R&D Building,” their movement is immediately restricted to only the very specific areas their compromised account has privileges for, severely limiting their ability to reach other sensitive R&D projects or other departments.
Conclusion
Both macro and micro segmentation are essential components of a robust Zero Trust Architecture. Macro segmentation provides the foundational, broad-stroke security at network layers 2, 3, and 4, while micro segmentation delivers the granular, workload-centric protection that extends to Layer 7 context. For cybersecurity professionals, the strategic implementation of both, with an emphasis on the fine-grained control offered by micro segmentation, is key to building resilient and adaptable security postures in today’s increasingly complex threat landscape. For organizations beginning their Zero Trust journey, achieving deep visibility into application communication flows is the critical first step toward designing and implementing an effective segmentation strategy.
Learn more about this and all 91 Target Level Zero Trust Activities at our page: Zero Trust Activities – Building a Modern Cybersecurity Posture.



