
From “Audit Theater” to Revenue Engine: Why Your GRC Program Needs a Customer Assurance Upgrade
November 24, 2025
Architecting Data for the AI Era
December 15, 2025Beyond Simulation: The Strategic Imperative of Adversarial Exposure Validation (AEV)
The cybersecurity industry has increasingly embraced proactive testing, moving past static vulnerability scans to dynamic attack emulation. Breach and Attack Simulation (BAS) marked a crucial step in this evolution, enabling security teams to routinely simulate individual adversary techniques and identify failures in their security controls. However, the modern threat landscape demands more than tactical, point-in-time assessments. The next strategic progression, Adversarial Exposure Validation (AEV), is emerging as the operational backbone for continuous threat exposure management, transforming how organizations measure and reduce risk.
The Evolution from BAS to AEV
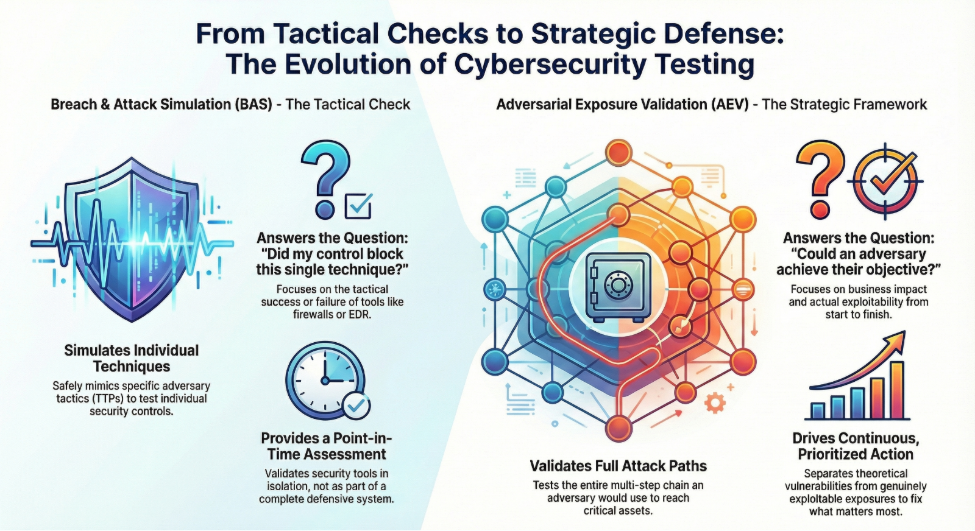
Breach and Attack Simulation (BAS) introduced the power of automated, continuous testing. BAS platforms safely mimic specific tactics, techniques, and procedures (TTPs), often aligned with the MITRE ATT&CK framework, to confirm if security controls (like EDR, firewalls, and SIEMs) are successfully detecting and preventing known adversarial actions. This provides a tactical validation of security tool efficacy.
Adversarial Exposure Validation (AEV) moves beyond this tactical approach to provide a strategic and holistic assessment. AEV is a comprehensive framework that integrates and automates the entire offensive security workflow. Where BAS often focuses on isolated techniques, AEV focuses on full, multi-step attack paths that an actual adversary would use to reach critical business assets.
The core difference is in the scope and objective. AEV combines continuous security control validation with automated penetration testing and red-teaming methodologies to deliver consistent, automated evidence of attack feasibility. It shifts the focus from “did my control block this single technique?” to “could an adversary successfully achieve their objective, and if so, what is the clear, exploitable path?” This change in perspective allows security teams to prioritize exposures based on actual exploitability and business impact, rather than on theoretical severity scores alone.
Why Continuous Validation is Non-Negotiable
The sheer complexity and dynamism of modern IT environments have made periodic, manual testing insufficient. Cloud migration, the proliferation of SaaS applications, and the constant patching and configuration changes within infrastructure mean that a security control that worked perfectly last week might be misconfigured or ineffective today. The adage, “security is a process, not a product,” has never been more relevant.
The importance of continuously validating your security controls cannot be overstated. Organizations spend significant capital on sophisticated security stacks—from endpoint detection and response (EDR) to next-generation firewalls (NGFW). Yet, without a mechanism to consistently prove that these investments are functioning as intended, that spend represents an unquantified risk. A security control that is misconfigured, has an expired license, or simply doesn’t log correctly provides a false sense of security.
AEV addresses this gap by creating a constant, automated feedback loop. It helps security teams:
- Filter the Noise: It separates the thousands of theoretical vulnerabilities (identified by traditional scanners) from the few high-priority exposures that are genuinely exploitable within the current environment.
- Validate Full Attack Chains: It tests the interconnectedness of security controls across the entire kill chain, revealing if an adversary can successfully move from initial access through to objective completion (e.g., data exfiltration).
- Drive Targeted Remediation: By providing proof of an exploit’s impact, AEV delivers actionable, contextualized remediation guidance, allowing teams to fix the security gaps that matter most and reduce real risk efficiently.
AttackIQ and the AEV Ecosystem

The move to Adversarial Exposure Validation has been spearheaded by innovative platform providers who recognize the need for continuous, threat-informed defense. AttackIQ is a key player in this evolution, providing a platform specifically designed to meet the demands of AEV. Their technology moves beyond simple simulations by operationalizing the MITRE ATT&CK framework to continuously validate security controls across the entire security program.
Our own experience with AttackIQ, even in a demo or testing environment, has illuminated the immediate benefits and significant potential of this approach. Setting up a controlled environment with existing security controls and then running various attack scenarios through AttackIQ provides a tangible understanding of how quickly gaps can be identified. This hands-on testing, even on a small scale, demonstrates how the platform can be used to validate security efficacy, fine-tune existing controls, and gain confidence in their ability to detect and prevent real-world threats. It’s a clear indicator of how AEV can transform theoretical security postures into demonstrably resilient defenses.
The AttackIQ platform allows organizations to leverage up-to-date threat intelligence and emulate known adversary behaviors at scale. By integrating discovery, prioritization, and automated validation, they provide the necessary tools for security teams to confidently measure the effectiveness of their defenses and track genuine risk reduction over time. This approach not only enhances the security posture but also provides clear, quantifiable data for CISOs to report to the board on the return on investment (ROI) of their security spending.
Operationalizing Security Readiness
AEV is intrinsically linked to the growing industry emphasis on Continuous Threat Exposure Management (CTEM), a Gartner-defined framework that calls for a structured, five-stage cycle: Scoping, Discovery, Prioritization, Validation, and Mobilization (Remediation). AEV serves as the engine for the “Validation” phase, delivering the evidence required to make the entire CTEM process proactive and effective.
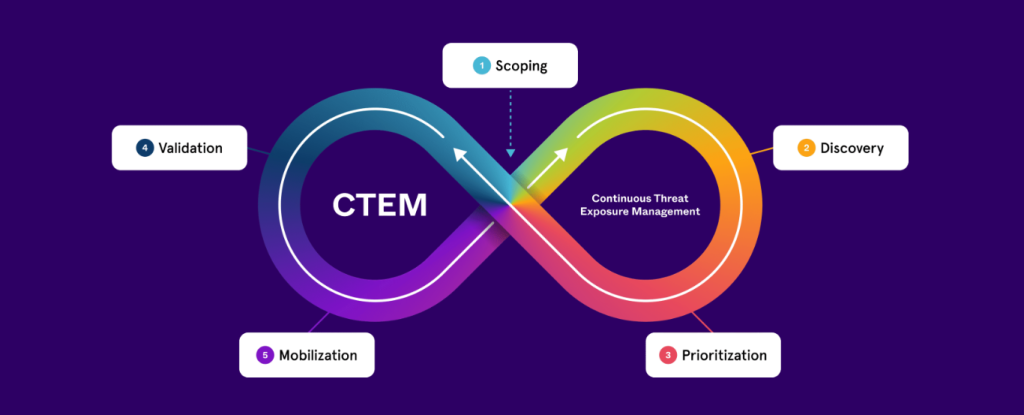
Credit: AttackIQ
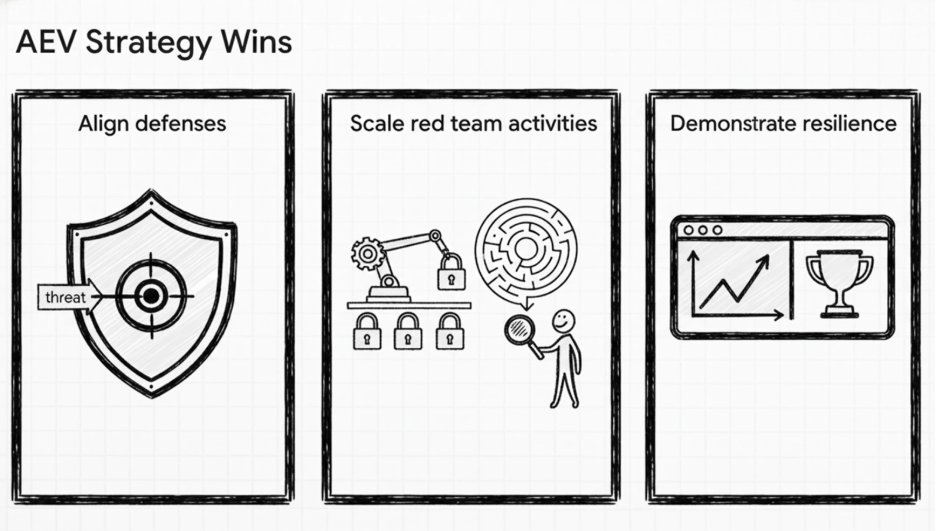
Adopting an AEV strategy allows security teams to:
- Align with Threat Intelligence: Automatically incorporate the TTPs of the most relevant threat actors targeting their industry, ensuring their defenses are tested against real and present dangers.
- Scale Red Teaming: Augment skilled, human-led red team exercises with automated testing, allowing human experts to focus on complex, bespoke scenarios while the platform ensures continuous coverage of foundational TTPs.
- Demonstrate Resilience: Generate clear, measurable metrics that prove the organization’s ability to prevent, detect, and respond to cyberattacks, building confidence among stakeholders and meeting stringent compliance requirements.
By shifting from periodic snapshots to continuous, adversary-focused validation, organizations transition from simply managing vulnerabilities to actively managing their exposure. Adversarial Exposure Validation is the essential next step for any organization committed to building a robust, evidence-backed, and truly resilient security posture.



