
A Deep Dive into Trellix Data Security
December 30, 2025
FRC Strengthens Leadership with Appointment of Technology Veteran Christopher Lynch to Board of Directors
January 13, 2026FRC’s Primer on the “Types” of Artificial Intelligence
If you’re evaluating AI for your agency or organization, you need to know that ‘AI’ isn’t one thing—it’s a diverse ecosystem of specialized technologies, each designed to solve specific types of problems. It is helpful to view these “types” as a stack: some serve as the mathematical foundation, while others act as the interface or the executive logic. This primer helps you match the right AI approach to your specific mission needs, whether that’s automating FOIA responses, improving service delivery, or modernizing legacy systems.
Understanding the distinctions between Machine Learning, Deep Learning, Computer Vision, Generative AI/LLMs, RAG, and Agentic AI is essential for moving past the “magic box” perception and toward a functional understanding of modern intelligence systems.
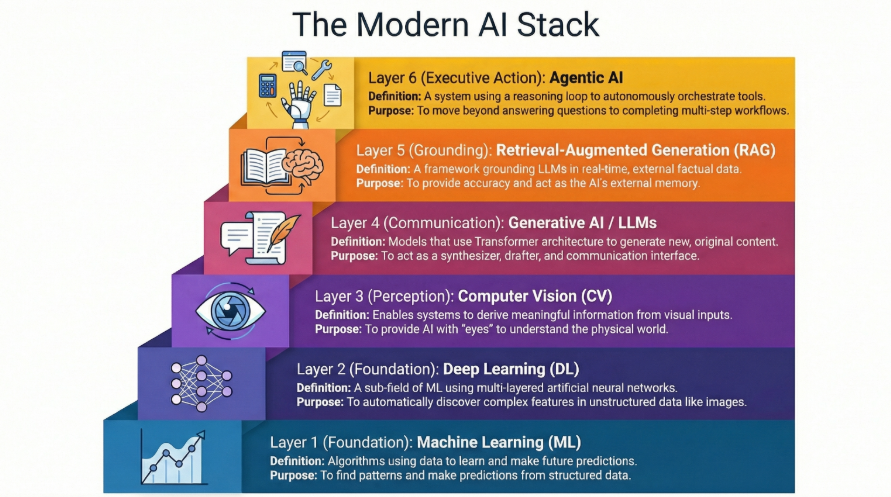
The Foundation: Machine Learning and Deep Learning
At the base of the entire ecosystem are Machine Learning (ML) and Deep Learning (DL). They are not “alternatives” to AI, because they are the engines that power it.
Machine Learning (ML)
Machine Learning is the practice of using algorithms to parse data, learn from it, and then make a determination or prediction about something in the world. Instead of hand-coding software with a specific set of instructions to accomplish a particular task, the machine is “trained” using large amounts of data and algorithms that give it the ability to learn how to perform the task.
Mathematically, ML is often about optimization and statistics. For example, an ML model in a SIEM platform might analyze user login patterns across thousands of variables like time of day, location, devices used, and data accessed. It establishes a baseline of ‘normal’ behavior for each user. When someone’s activity deviates significantly from their pattern (logging in from an unusual country at 3 AM and accessing sensitive files), the model flags it as a potential compromised account.
Deep Learning (DL)
Deep Learning is a specialized subfield of Machine Learning. It utilizes Artificial Neural Networks, which are algorithms inspired by the structure and function of the human brain. While traditional ML models often require a human to manually “feature engineer” (tell the model which data points are important), Deep Learning models can automatically discover the features needed for classification.
Deep Learning is powered by Artificial Neural Networks, which are layers of interconnected nodes. Data passes through these layers, undergoing non-linear mathematical transformations at each step. Through a process called backpropagation, the network adjusts the “weights” of its connections based on how far off its final output was from the target. The ‘Deep’ refers to the many hidden layers that allow the model to handle high-dimensional, unstructured data like network traffic patterns, raw executable code, or security log entries. For instance, next-generation endpoint protection uses Deep Learning to analyze the actual structure and behavior of files at the binary level, detecting malware variants that have never been seen before, expanding past what traditional signature-based antivirus can do.
Specialized Perception: Computer Vision
If Deep Learning provides the “brain,” Computer Vision (CV) provides the “eyes.” Computer Vision is a field of AI that enables computers and systems to derive meaningful information from digital images, videos, and other visual inputs.
How it Works
The technical workhorse of CV is the Convolutional Neural Network (CNN). Unlike standard neural networks that treat images as flat arrays of numbers, CNNs use “filters” to scan images in small sections. This allows the model to preserve the spatial relationship between pixels, identifying edges in the first layer, shapes in the second, and complex objects (like a human face or a brand logo) in the deeper layers.
Purpose
The purpose of Computer Vision is to bridge the gap between physical reality and digital data. In a professional context, this is used for everything from analyzing security camera feeds in real-time to detect unauthorized access patterns, to document verification systems that can identify forged credentials or tampered IDs, to physical-digital security correlation where CV systems track individuals moving through facilities and cross-reference with access control logs.
The Communicators: Generative AI and LLMs
Generative AI refers to models that can create new content, with Large Language Models (LLMs) being the most prominent type focused on text.
How it Works
Modern LLMs are built on the Transformer architecture. The key technical breakthrough here is the Self-Attention mechanism, which allows the model to weigh the importance of different words in a sentence simultaneously. When you provide a prompt, the model converts words into tokens and uses its billions of parameters to calculate the statistical probability of the next token in the sequence.
Purpose
In cybersecurity operations, LLMs are increasingly used to translate complex threat intelligence into actionable summaries, draft incident response reports, and help security analysts quickly understand what a sophisticated attack chain actually did, which saves analysts hours of work and helps newer analysts get up to speed.
The Library: Retrieval-Augmented Generation (RAG)
Generative models are often limited by their “knowledge cutoff”… they only know what they were trained on. Retrieval-Augmented Generation (RAG) is a framework that grounds these models in real-time, factual data.
How it Works
RAG utilizes Vector Databases and Embeddings. External documents (like a company’s internal security manuals) are converted into high-dimensional numerical vectors. For example, when a security analyst asks an AI assistant ‘What’s our policy on cloud data encryption?’, RAG retrieves the exact relevant sections from the organization’s security documentation rather than having the AI guess based on generic best practices.
Purpose
RAG provides accuracy and grounding. It acts as the AI’s external memory, ensuring the system remains truthful and up-to-date without needing to constantly retrain the underlying model.
The Manager: Agentic AI
The most advanced layer is Agentic AI. While an LLM is a tool you use, an AI Agent is a system that uses tools on your behalf.
How it Works
An AI Agent uses a “reasoning loop,” often following a logic pattern like ReAct (Reason + Act). The agent receives a high-level goal, breaks it into sub-tasks, and decides which “tools” (APIs, calculators, or web browsers) it needs to call. It monitors its own progress and can “reflect” on errors, adjusting its plan mid-stream if a specific action fails.
Purpose
The purpose of Agentic AI is autonomous orchestration. It moves beyond answering questions to completing multi-step workflows, completing multi-step workflows, such as triaging a security alert, gathering context from multiple tools (SIEM, EDR, threat intelligence), determining if it’s a true positive, and recommending specific remediation steps. Of course, human oversight still remains essential for any actions that could impact operations.

The Collaborative AI Workflow
To see how these ‘types’ serve a unified purpose, imagine a modern Security Operations Center (SOC):
- Computer Vision monitors the facility’s physical security cameras to detect tailgating or unauthorized access attempts at building entrances. When someone bypasses the badge reader by following closely behind an authorized employee, the CV system flags the anomaly.
- Machine Learning analyzes network traffic patterns across the organization’s infrastructure. It has established baseline behaviors for every user and system including typical data volumes, common access patterns, and normal working hours. When an employee account suddenly begins uploading gigabytes of data to an external cloud service at 2 AM on a Sunday, the ML model flags this as anomalous behavior requiring investigation.
- Deep Learning powers the endpoint detection and response (EDR) platform monitoring every workstation and server. When a user downloads a file, the deep learning model analyzes the file’s actual structure rather than just it’s signature against a database of known malware, examines how it attempts to execute, and recognizes patterns consistent with malicious code even if this specific variant has never been seen before.
- Agentic AI receives the alert about the suspicious file from the EDR system. Rather than simply notifying an analyst, it “reasons” that additional context is needed to determine severity. It “acts” by automatically querying the SIEM for any related network activity from that endpoint, checking threat intelligence feeds to see if similar file hashes have been reported elsewhere, and correlating the timeline with the physical security alert about the tailgating incident thirty minutes earlier. It discovers these events involve the same employee badge number. The agent escalates this as a high-priority incident with all relevant context assembled, rather than generating three separate low-priority alerts that an analyst would need to manually correlate.
- RAG & LLMs handle the final synthesis and communication layer. When the CISO arrives Monday morning and asks, “What’s the status of the weekend security incident?”, the LLM retrieves the complete incident timeline via RAG, pulling from EDR logs, SIEM entries, the physical security system, and the agent’s investigation notes. It generates a concise executive summary: “A potential insider threat was detected Saturday evening. An individual used badge #4782 to tailgate into Building C at 11:47 PM, then the associated user account exhibited data exfiltration behavior at 2:13 AM. The endpoint was automatically isolated, the badge was disabled, and HR has been notified. No sensitive data left the network. Full incident report attached.”
This workflow demonstrates why understanding the distinctions between AI types matters: each layer contributes a specific capability. Computer Vision provides sensory input from the physical world. Machine Learning establishes behavioral baselines and detects deviations. Deep Learning handles complex pattern recognition in unstructured data. Agentic AI orchestrates the investigation across multiple tools. And Generative AI with RAG translates technical findings into actionable business intelligence.
No single AI type could accomplish this alone. The ML system might have flagged the unusual network activity, but without the agent to correlate it with physical security and endpoint data, it would have appeared as an isolated anomaly rather than a coordinated incident. The LLM could summarize information, but without RAG grounding it in actual log data, it might generate a plausible-sounding but factually incorrect report.
Conclusion
The effectiveness of an AI strategy depends on selecting the right tool for the right layer of the problem. Use Machine Learning for structured data predictions and behavioral analysis, Computer Vision for physical security integration, Deep Learning for pattern recognition in complex data like malware, Generative AI for content synthesis and operational efficiency, RAG for factual grounding in organizational knowledge, and Agentic frameworks for orchestrated multi-tool workflows.
Would you like to discuss how AI can support your mission and agency? Seeking to learn more about how your tools can benefit from using AI?
Reach out to our team today to schedule a discussion.



