
Federal Resources Corporation Announces Rebrand to FRC, Reflecting Expansion Beyond Federal Markets
November 18, 2025
From “Audit Theater” to Revenue Engine: Why Your GRC Program Needs a Customer Assurance Upgrade
November 24, 2025Understanding Data Loss Prevention (DLP)
Modern security strategy, particularly a Zero Trust Architecture (ZTA), is built on a single, fundamental truth: data is the center of the security universe. This data is the “gold” that drives innovation and maintains customer relationships; it’s the “confidential information” and “intellectual property” that is the ultimate target of any attack.
Every other pillar of a Zero Trust model—Identity, Devices, Networks, and Applications—acts as a sophisticated set of guards. Their primary purpose is to continuously verify who and what should be allowed to get near that data.

But a critical question remains: What happens when a trusted identity on a verified device tries to move that data where it shouldn’t go? Whether it’s an accidental error or a malicious, intentional leak, this is the final-line-of-defense question answered by Data Loss Prevention (DLP). DLP is a comprehensive strategy, supported by a set of tools and processes, designed to ensure that sensitive data is not exfiltrated or leaked from an organization.
What Does a Successful DLP Solution Do?
A truly effective DLP solution provides a multi-layered defense that integrates with how your organization works. A successful solution must:
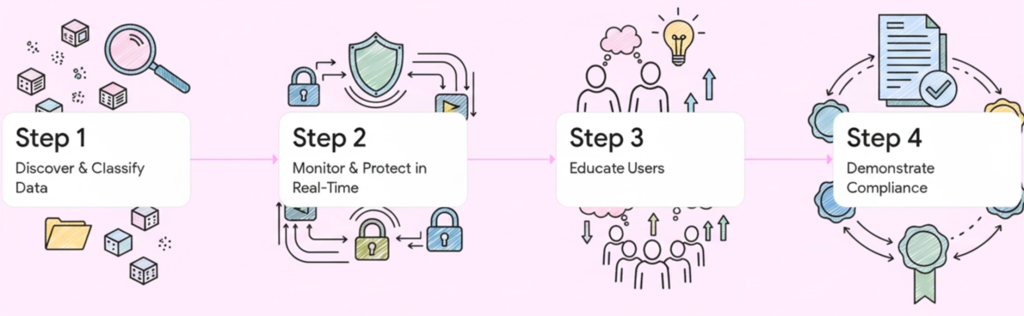
- Discover and Classify Data: You can’t protect what you don’t know you have. A strong DLP solution first scans your environment to find sensitive data wherever it rests—on laptops, in servers, or in files and folders. It then classifies this data based on standard rules (like Personal Information, Personal Health Information, or Payment Card Information) or custom rules unique to your organization’s intellectual property.
- Monitor and Protect in Real-Time: Once data is classified, the solution must monitor its use. This means protecting sensitive data from unauthorized transfer, duplication, or even printing. This protection needs to apply across all potential leak points, including email, web browsers, and physical devices.
- Educate Users (Not Just Block Them): Many data leaks are accidental. A smart DLP solution doesn’t just block an action; it educates the user. It can provide customizable pop-up notifications to inform an employee that their action is violating policy. By asking for justification, it turns a potential mistake into a valuable, real-time coaching moment.
- Demonstrate Compliance: With regulations like GDPR, HIPAA, and others, proving you are protecting data is just as important as protecting it. A successful DLP solution provides the out-of-the-box policies, auditing, and forensic reporting needed to demonstrate compliance to regulators. A high-stakes example of this is within the U.S. Department of Defense (DoD). Directives like OPORD-8600 mandate strict ‘Comply-to-Connect’ (C2C) policies. DLP is a critical component of the Command Orchestrated Readiness and Assessments (CORA) audits used to verify this compliance, covering data at rest, in use, and in motion. A strong DLP solution is therefore essential for DoD agencies to meet these stringent readiness and security requirements.
The Trellix Approach to Data Loss Prevention
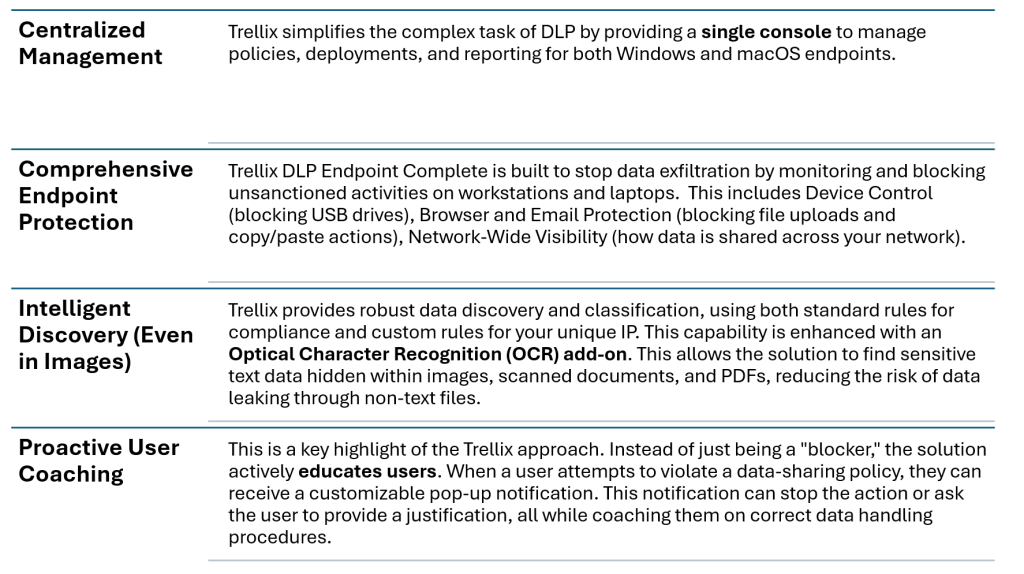
Trellix Data Loss Prevention (DLP) is designed to provide this comprehensive protection, with a strong focus on the most vulnerable part of any network: the endpoints. Here’s how its capabilities align with the goals of a successful DLP strategy:

Streamlined Compliance
For organizations struggling to meet regulatory demands, Trellix provides out-of-the-box policies that align with common compliance frameworks. This, combined with powerful auditing and reporting tools, makes it simpler to conduct forensics and demonstrate compliance when needed. This is particularly relevant for high-compliance environments like the DoD, where Trellix’s endpoint protection and DLP capabilities are used to help achieve readiness for OPORD-8600 and CORA audits.
In short, Data Loss Prevention is no longer an optional “add-on” but a foundational component of any serious security strategy. A modern solution, like that from Trellix, moves beyond simple blocking to provide intelligent discovery, comprehensive endpoint control, and proactive user education, ensuring your organization’s “gold” stays safe.
FRC is your trusted partner
- As a DoD ESI partner on SEWP, FRC delivers cost savings, compliance assurance, and procurement efficiency.
- Since 2024, we have helped 20+ DoD customers maximize their current Trellix investments.
- Read our White Paper about Data Loss Protection (DLP) and CORA.
Learn more about this and all 91 Target Level Zero Trust Activities at our page: Zero Trust Activities – Building a Modern Cybersecurity Posture.



