
How Continuous Monitoring and Validation Actually Work in Governance, Risk, and Compliance (GRC) Tools
October 27, 2025
Macro vs. Micro Segmentation in a Zero Trust Architecture: Drawing the Fences
November 12, 2025Zero Trust Target Level Requires Procurement & Implementation of UEBA Tooling
Zero Trust demands continuous verification, and User and Entity Behavior Analytics (UEBA) provides the intelligence to make that verification meaningful. It answers the critical question that rules-based systems can’t: “Is this behavior normal?” By using machine learning to build a baseline of typical activity for every user and entity, UEBA provides the essential context to automatically spot high-risk deviations. It’s the engine that moves Zero Trust to a continuously enforced, automated reality, allowing teams to find the subtle signals of a genuine threat in a sea of data.
UEBA is critical to several DoD Zero Trust Target Level Activities, specifically
These activities lay the foundation for UEBA to be used in more decision making at the Advanced level of implementing Zero Trust (e.g., using UEBA as part of Mult-Factor Authentication, Privileged Access Management, Just-in-Time and Just Enough Access decisions, advanced Device Authorizations).
The Limits of Rule-Based Verification
In a Zero Trust environment, every access request, every API call, and every data transfer generates a log. A powerful SIEM, like Elastic SIEM, is essential for aggregating this mountain of data from diverse sources including cloud platforms, identity providers, endpoints, and network appliances.
The traditional approach to UEBA would be to write correlation rules to detect suspicious activity. For example, a rule might flag a user logging in from two different countries within an hour. While useful, this method has significant limitations:
- It can’t detect the unknown. Rule-based systems are great at catching threats we already know how to look for. They are ill-equipped to identify novel attack techniques or sophisticated attackers who intentionally operate below the threshold of simple rules.
- It lacks context. A rule might see a user accessing a sensitive database as “allowed” based on their permissions. It doesn’t know if that user has ever accessed that database before, if they’re doing it at an unusual time, or if their endpoint is behaving abnormally.
- It generates alert fatigue. As the number of rules grows to cover more scenarios, so does the volume of false positives. Security analysts spend too much time chasing ghosts, dulling their response to real incidents.
Zero Trust demands more than just a yes/no check at the point of access… it requires continuous, context-aware verification of behavior.
UEBA: Establishing the Baseline of “Normal”
UEBA changes the security paradigm from “looking for bad” to “understanding normal.” It uses machine learning algorithms to analyze the vast datasets collected by your SIEM and automatically build a behavioral baseline for every single user and entity (e.g., servers, endpoints, applications) on your network.
This baseline is a rich, multi-dimensional profile that answers questions like:
- What applications and data does this user typically access?
- What time of day and from what locations do they usually work?
- Which servers does this endpoint normally communicate with?
- What is the normal volume of data upload/download for this user?
Once this baseline of normal behavior is established, the UEBA engine, often powered by the machine learning features within Elastic, can instantly spot meaningful deviations. It’s flagging a behavioral anomaly rather than just an event, and assigning it a risk score based on the severity of the deviation.
Elastic ML: The Unsupervised Engine Powering UEBA
UEBA is precisely where the native machine learning capabilities of Elastic SIEM provide the critical advantage. The power of the Elastic Stack lies its ability to ingest and search massive volumes of data and to understand that data through integrated, unsupervised machine learning.
“Unsupervised” is the operative word. Instead of waiting for an analyst to write a rule defining “bad,” Elastic’s ML autonomously models the behavior of every user and entity across your dataset. It learns the unique “heartbeat” of your organization like the typical login times for a specific administrator, the normal data flows from a production server, the common processes run on an endpoint.
This capability is so powerful for three key reasons:
- It’s Automated and Continuous: It dynamically builds and updates these behavioral baselines in real-time. This is a living model that adapts as your organization changes.
- It Detects “Unknown Unknowns”: Because the ML is focused on defining “normal,” it excels at spotting novel attack patterns that have no predefined signature. An attacker doesn’t need to trigger a known-bad IOC… they only need to deviate from the established baseline, and Elastic will flag the anomaly.
- It Provides Context-Rich Alerts: Elastic ML provides a statistical “anomaly score” that highlights how unusual a specific behavior is. This immediately separates a critical deviation from benign statistical noise, drastically reducing alert fatigue.
This built-in ML is the “analytics” engine in User and Entity Behavior Analytics. It transforms UEBA from a simple concept into a powerful, automated threat-hunting capability directly within your SIEM.

Detecting Threats Traditional Methods Miss
The true power of UEBA is its ability to connect seemingly disparate, low-level events to uncover sophisticated attacks that would otherwise fly under the radar.
Scenario 1: The Compromised Credential
An attacker gains access to a project manager’s credentials via a phishing attack. The initial login from a new device might trigger a basic alert, but it could easily be dismissed. The attacker then proceeds cautiously.
- Traditional Method: The attacker’s actions like accessing project files are all technically “authorized” for the project manager’s account. As long as they don’t trigger a specific rule (like large-scale data exfiltration), their activity goes unnoticed.
- With UEBA: The UEBA engine detects a cluster of anomalies. The login is from a new device and geolocation. The user is accessing files they haven’t touched in six months. The time of access is 2:00 AM, whereas they normally work 9-to-5. While each event alone might be weak, UEBA’s machine learning models see the combined pattern as highly improbable and flag the user account with a high-risk score, alerting analysts to a likely compromise.
Scenario 2: The Malicious Insider
A disgruntled developer plans to steal proprietary source code before leaving the company. They know that downloading the entire repository at once would be too obvious.
- Traditional Method: The developer downloads small chunks of code over several weeks. Each individual action is small and well within their permissions, so no rules are triggered.
- With UEBA: The developer’s baseline shows they typically access and modify code, but rarely perform bulk downloads. The UEBA model detects a subtle but steady increase in their data access volume directed at the code repository. This deviation from their established peer group and their own historical behavior creates an escalating risk score, allowing security to intervene before the intellectual property walks out the door.
Scenario 3: Lateral Movement
An attacker compromises a front-end web server. Their goal is to move laterally through the network to reach a critical database server.
- Traditional Method: Security might see some unusual port scanning from the web server, but without a specific rule against it, this activity might be lost in the noise of network traffic logs.
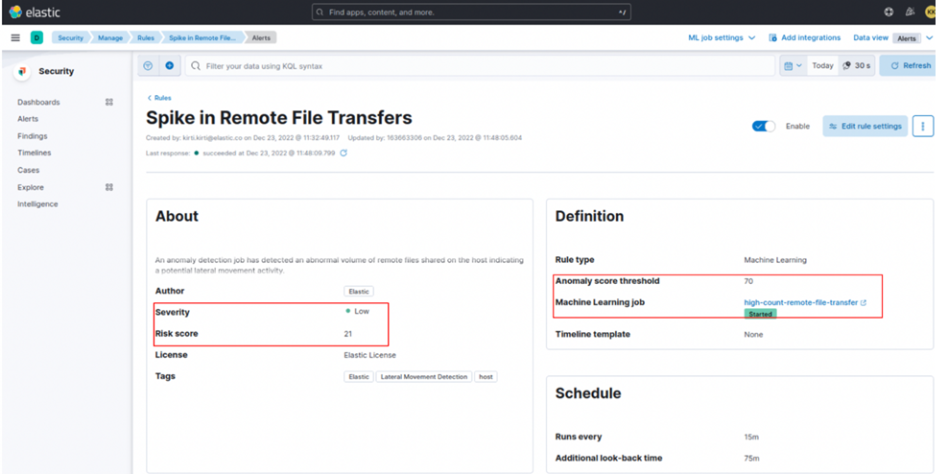
- With UEBA: The UEBA engine has a behavioral baseline for the web server entity. It knows this server normally only communicates with a specific application server on port 443. When it suddenly starts attempting to connect to dozens of other internal servers on different ports, UEBA immediately identifies this as anomalous entity behavior (a classic sign of reconnaissance and lateral movement) and triggers a high-priority alert.
Conclusion: Intelligence is the Keystone of Zero Trust
A Zero Trust architecture provides the necessary framework for modern security, but frameworks alone don’t stop attackers. True security is achieved through intelligent and continuous verification. By integrating UEBA capabilities, such as the powerful machine learning features within Elastic SIEM, organizations can move beyond simple, static checks. They can understand the context behind every action, detect subtle deviations that signal a sophisticated attack, and automate responses to neutralize threats in real-time. UEBA the essential intelligence layer that makes Zero Trust truly effective.



