
Shifting Security Left: Integrating Security into the SDLC with a DevSecOps Factory
September 23, 2025
What You Need to Add to your IT Inventory List to Meet Target-Level Zero Trust Posture
October 7, 2025Why Zero Trust Needs Automation to Work
Security teams are stretched thin. They are tasked with defending a constantly expanding digital footprint while wrestling with a flood of alerts and a mountain of repetitive manual tasks. This operational drag not only leads to burnout but also slows down critical security functions, from deploying new services to responding to active threats. The solution isn’t just to buy more tools; it’s to work smarter.
The key to unlocking efficiency and elevating your security posture lies in strategic automation. But effective automation doesn’t start with a product—it starts with a plan. In fact, this is a key activity in DoD’s Zero Trust Architecture: Zero Trust Activity 6.2.1 – Task Automation Analysis. By systematically analyzing your existing security tasks, you can build a blueprint for an automation strategy that optimizes mission-critical processes, reduces time and resources spent, increases accuracy by limiting human error, and fundamentally accelerates incident response.
Why Automation is the Engine of Zero Trust
A Zero Trust Architecture is dynamic by nature. It relies on continuous verification and enforcement of policies across users, devices, and applications. Relying on manual operations to manage this constant cycle is unsustainable and destined to fail. Automation is the engine that makes Zero Trust work at scale, transforming static policies into a dynamic, active defense. It ensures that security controls are applied consistently, 24/7, without the inherent risk of human error.
The Blueprint: A Guide to Task Automation Analysis
Before you can automate, you must understand. A Task Automation Analysis, like the one detailed in the DoD’s Zero Trust roadmap (Activity 6.2.1), provides a structured framework for this discovery. This process mandates that organizations systematically identify and enumerate all security-related task activities, both manual and automated. This holistic discovery forces a comprehensive look at all security-related tasks, not just the obvious ones, and can uncover hidden, repetitive tasks currently handled manually across various teams.
Once identified, these tasks are categorized into clear automated and manual groups. The critical next step is to analyze the manual activities for their potential for automation or even complete elimination. This prioritization allows security teams to focus their automation efforts on areas with the greatest impact, such as those with high mission-criticality, high frequency, or a high potential for human error.
For a more detailed guide on how to achieve these goals, read our analysis of Activity 6.2.1 here.
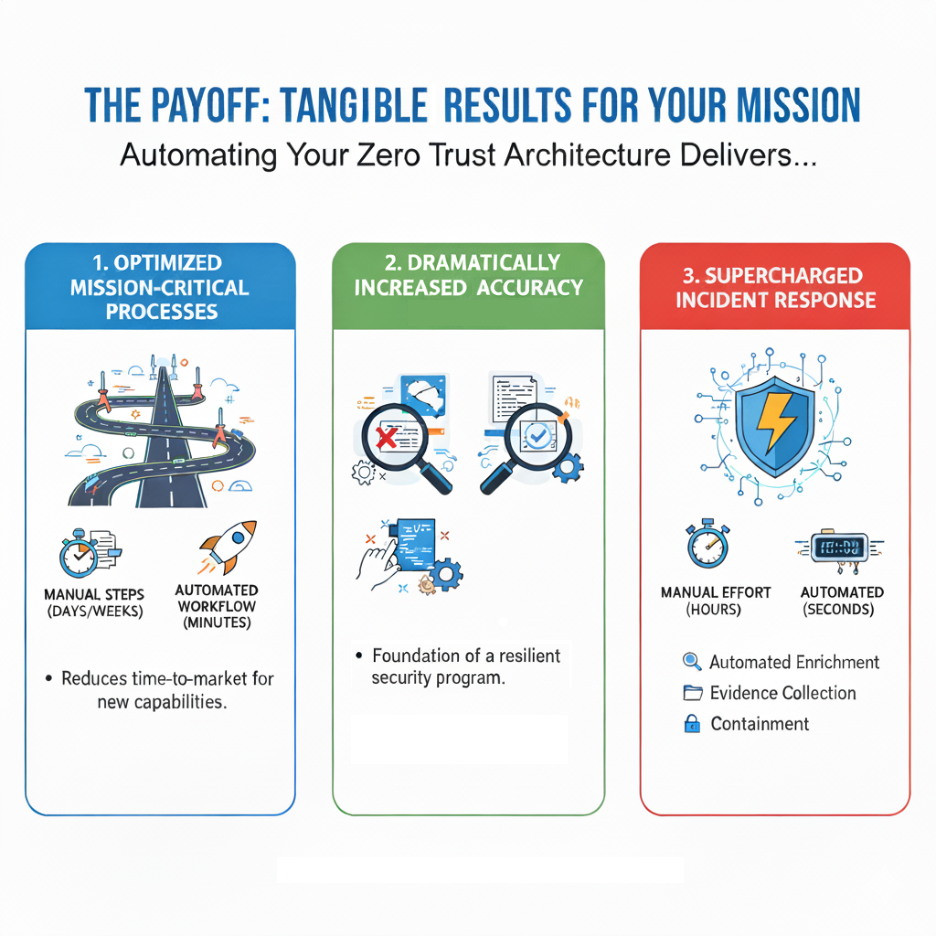
The Payoff: Tangible Results for Your Mission
Conducting this analysis creates a direct path to achieving your strategic goals.
- Optimized Mission-Critical Processes: Consider the process of deploying a new application. Manually, this can involve dozens of steps and multiple teams to configure network rules, set identity permissions, and run vulnerability scans, often taking days or weeks. An automated workflow, designed through this analysis, can orchestrate these tasks in minutes, drastically reducing time-to-market for new capabilities.
- Dramatically Increased Accuracy: Manual tasks are prone to error. An analyst working a long shift might miss a critical alert, or a technician might enter an incorrect IP address in a firewall rule. Validated automation executes a task perfectly every time, removing the risk of typos, missed steps, and configuration drift. This consistency is the foundation of a resilient and auditable security program.
- Supercharged Incident Response: When an incident occurs, time is your most critical asset. Automation can execute response “playbooks” at machine speed, turning a multi-hour manual effort into a sub-minute automated reaction. Examples include:
- Automated Enrichment: Instantly enriching an alert with threat intelligence and user context.
- Evidence Collection: Automatically pulling logs and forensic data from an endpoint upon detection.
- Containment: Isolating a compromised host from the network or suspending a user account to stop an attack in its tracks.
From Reactive to Proactive
A Task Automation Analysis is the strategic foundation for transforming to a proactive, automation-driven one is essential for modern defense. It forces you to look critically at your operations, identify the true sources of risk and inefficiency, and build an automation program that is secure, effective, and directly focused on protecting what matters most. By thinking before you automate, you ensure your efforts will build a more resilient, efficient, and mission-ready security enterprise.



